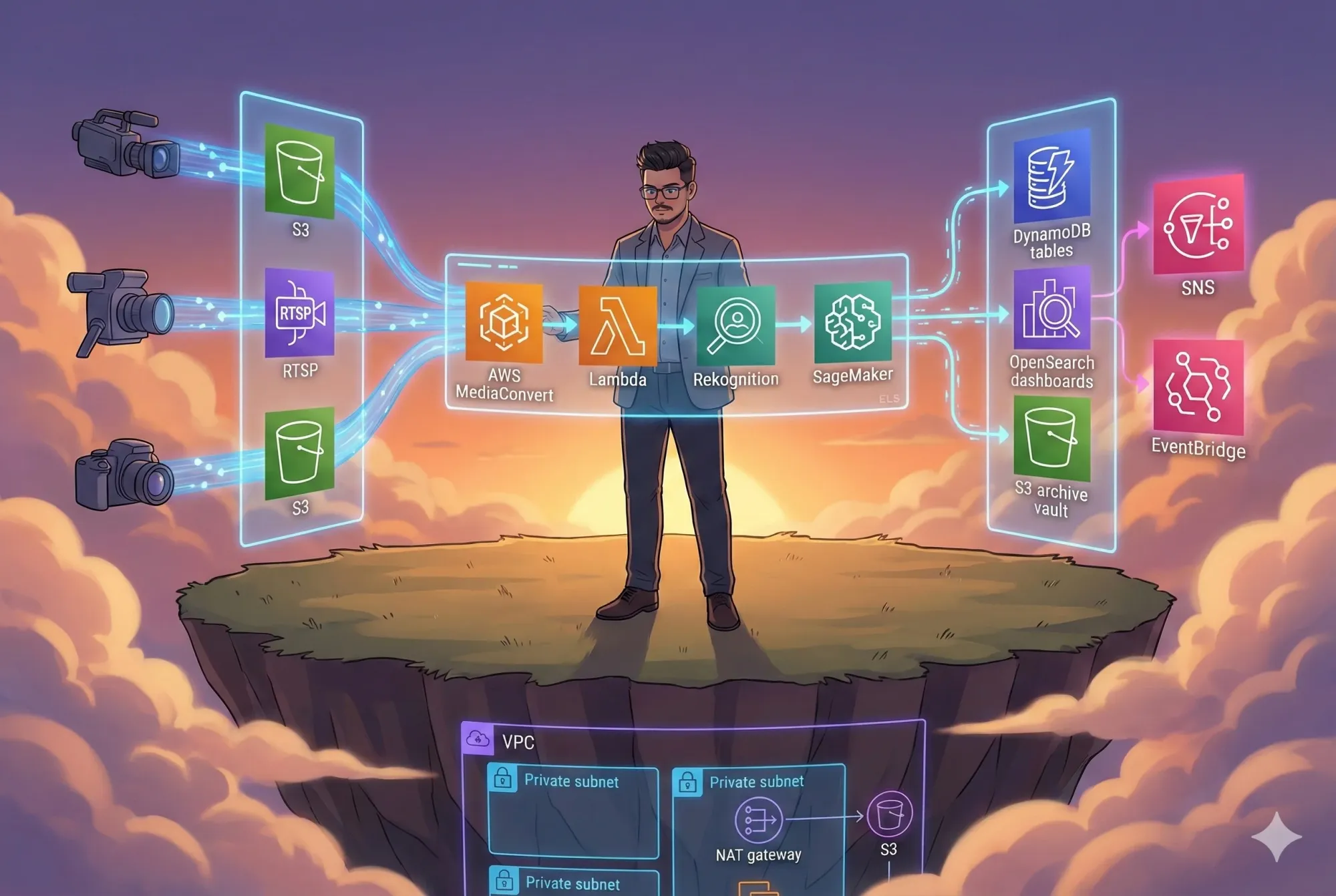
Building a Cloud-Native SIEM on AWS: The Story of How Modern Security Comes Together
A cloud-native SIEM on AWS delivering real-time threat detection, log correlation, automated incident response, and compliance. This overview highlights how InfraTales uses VPC isolation, scalable compute, and advanced monitoring to secure modern cloud environments.

In every growing cloud environment, there’s a moment when the number of logs, alerts, flows, and application traces becomes too massive for any human or traditional monitoring tool to handle. The moment when dashboards feel like static paintings instead of real insight. The moment when an organization needs more than logging, it needs awareness.
This is the moment a SIEM steps into the story.
The InfraTales SIEM Platform isn’t just another stack of AWS services wired together. Think of it as the nervous system of a cloud ecosystem, a system that senses, correlates, analyzes, and responds to signals in real time. A system that can protect, learn, and tell the truth about what’s unfolding inside your AWS environment.
Let’s take a journey through this platform not as a list of steps, but as a story of how modern security is built, seen through the lens of cloud reality, engineering decisions, and the invisible machinery running beneath your applications.
The World Behind the Console
Imagine your AWS environment as a vast digital landscape applications running across compute clusters, serverless functions firing off invisible workflows, data flowing quietly between services, and logs accumulating like grains of sand.
Inside this living ecosystem, millions of micro-events happen every minute:
- A user authenticates
- A container spins up
- A Lambda function processes a request
- An IAM role is assumed
- A suspicious network packet appears
- An RDS query takes too long
- A VPC Flow Log shows unexpected traffic
What looks like noise to a human is full of meaning to a SIEM.
So the InfraTales SIEM platform positions itself at the center of this ecosystem, quietly watching everything, collecting, correlating, detecting, and reacting in real time.
This is the architecture supporting that mission:

The Foundation: A VPC Built Like a Secure City
Every SIEM needs a strong foundation for the network. Imagine your AWS VPC not as a mere CIDR block, but as a carefully structured security district.
Public subnets become the city gates, the only part exposed to the outside world. Private subnets become your operational districts where the SIEM analyzes logs, runs engines, correlates events, and triggers actions. Database subnets become the vaults, deeply buried and inaccessible from the internet.
Here’s a glimpse of that city map:

Nothing in the data plane can talk to the internet. The SIEM’s core is dark intentionally. Isolation is the first chapter in the story of trust.
When Logs Start Talking
Logs are the language of your infrastructure.
Some logs whisper:
“User logged in.”
Some shout:
“Strange inbound packet detected on port 22.”
Some warn you:
“IAM key rotated outside standard policy.”
But individually, these logs don’t tell a full story. Meaning emerges only when events come together, when separate signals align into a pattern.
This is where the SIEM begins its real job.
The Journey of a Single Event
Picture this: an authentication request comes into the system. Nothing unusual at first glance. But the SIEM doesn’t see a single event; it sees a trajectory.
It follows this flow:

This is more than a login flow; it’s a story arc.
One where the SIEM watches every stage, making sure each chapter makes sense.
If anything looks suspicious, a login from an unexpected region, an API key used at odd hours, or elevated privileges assumed too frequently, the SIEM connects those threads and raises a flag.
The Brain Behind Correlation
Correlation is where SIEM becomes intelligence.
The platform understands relationships:
- A VPC Flow Log showing an inbound port scan
- Followed by an IAM role modified by a user
- Followed by an ECS task reporting unusual CPU spikes
- Followed by an API call from an unknown IP
Structurally, these are separate events.
Narratively, this is a developing attack.
The SIEM stitches this storyline together.
How it builds correlations:
- Aurora/RDS stores normalized logs for deep search
- DynamoDB holds state and real-time correlation maps
- Lambda performs enrichment & threat intel lookups
- S3 stores immutable long-term log archives
- OpenSearch (optional) powers security analytics dashboards
Together, they transform raw logs into narratives of behavior.
When Threats Knock on the Door
Every SIEM story has a conflict.
And in cloud environments, the antagonists range from harmless bots to sophisticated threat actors.
When an unusual pattern emerges, say, repeated failed logins from diverse geographic locations, the SIEM doesn’t just alert.
It evaluates…
- Does this match any IOC (Indicator of Compromise)?
- Has this IP been seen before?
- Is this user behavior normal?
- Are there signs of lateral movement?
- Is there a privilege escalation attempt?
Depending on the severity, it may:
- Add the IP to the AWS WAF blocklist
- Disable a suspicious IAM role
- Rotate access keys
- Isolate an EC2 instance
- Trigger an incident response Lambda
- Notify a security engineer via SNS / Slack
The platform isn’t passive; it takes action.
Observability: Seeing the Story From Above
A SIEM without observability is like reading a book in the dark.
So InfraTales includes full-stack observability:
CloudWatch Metrics
Tracks everything from CPU to ingestion rates.
X-Ray Tracing
Shows the full call flow, invaluable during investigations.
SNS Alerts
Deliver alerts the moment a story takes a bad turn.
Observability isn’t just logging; it’s being able to explain what’s happening across the system in a way that humans can understand. After all, human analysts are the editors of the SIEM’s storylines.
The Invisible Machinery: CI/CD and Deployment
Deploying a SIEM is a sensitive moment. Infrastructure changes affect logs, ingestors, correlations, alerts, and your entire security posture.
That’s why InfraTales uses a careful deployment story:

Canary deployments turn releases into controlled chapters, testing new behavior with real traffic, but only a small piece of it.
If the new version behaves badly? The story rewinds automatically.
Security: The Theme Tying It All Together
The SIEM platform doesn’t just enforce security, it embodies it.
Encryption Everywhere
- TLS 1.3 in transit
- KMS-encrypted databases
- Encrypted S3 buckets
- Secrets Manager for credentials
IAM Least Privilege
Roles are designed like characters:
Each one has a purpose, nothing more.
WAF at the Gates
Filtering out malicious traffic long before it reaches your compute.
CloudTrail Recording the Story
Every API call is captured.
Every decision logged.
Every deviation is noticeable.
Cost, Because Every Story Has Constraints
Security doesn’t need to be expensive.
It needs to be intelligent.
This design intentionally balances:
- Reserved Instances for predictable workloads
- Auto-scaling for unpredictable ones
- Spot instances for low-priority tasks
- Intelligent-tiering for log archival
- Automated shutdown for non-prod environments
Two versions of the story exist:
| Environment | Monthly Cost |
|---|---|
| Dev | $190–550 |
| Prod | $900–4000 |
A fair trade for an always-on security brain.
Who This Platform Is Meant For
This SIEM story resonates with:
- Security teams building their first cloud-native SIEM
- DevOps engineers seeking observability excellence
- Compliance teams need detailed audit trails
- Cloud architects wanting a reference blueprint
- Organizations seeking independence from costly commercial SIEMs
The Epilogue: Why This SIEM Matters
In the end, security isn’t about tools; it’s about understanding.
A SIEM gives shape to the hidden stories inside your cloud infrastructure.
It reveals motives, behaviors, anomalies, and connections.
It turns noise into narrative, and narrative into action.
The InfraTales SIEM Platform doesn’t force you to adopt a vendor’s vision.
It gives you your own.
A platform you can shape, audit, trust, and expand built entirely on AWS, powered by Terraform, designed with clarity, and architected with real-world constraints in mind.
Security isn’t a feature.
It’s a story we must continuously write.
And this SIEM gives you the pen.
Official References & Documentation
🔗 VPC - https://docs.aws.amazon.com/vpc/latest/userguide/what-is-amazon-vpc.html
🔗 VPC Flow Logs - https://docs.aws.amazon.com/vpc/latest/userguide/flow-logs.html
🔗 CloudTrail - https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-user-guide.html
🔗 CloudWatch Logs - https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/AnalyzingLogData.html
🔗 CloudWatch Metrics - https://docs.aws.amazon.com/cloudwatch/
🔗 AWS Lambda - https://docs.aws.amazon.com/lambda/latest/dg/welcome.html
🔗 DynamoDB - https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/Welcome.html
🔗 Aurora/RDS - https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/Welcome.html
🔗 Amazon S3 - https://docs.aws.amazon.com/AmazonS3/latest/userguide/Welcome.html
🔗 AWS OpenSearch - https://docs.aws.amazon.com/opensearch-service/latest/developerguide/what-is.html
🔗 AWS IAM - https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.html
🔗 AWS KMS Encryption - https://docs.aws.amazon.com/kms/latest/developerguide/overview.html
🔗 AWS WAF - https://docs.aws.amazon.com/waf/latest/developerguide/what-is-aws-waf.html
🔗 AWS GuardDuty - https://docs.aws.amazon.com/guardduty/latest/ug/what-is-guardduty.html
🔗 AWS SNS - https://docs.aws.amazon.com/sns/latest/dg/welcome.html
🔗 AWS X-Ray - https://docs.aws.amazon.com/xray/latest/devguide/aws-xray.html
🔗 Terraform AWS Provider - https://registry.terraform.io/providers/hashicorp/aws/latest/docs
Repository Details
👉 GitHub Repository:
https://github.com/InfraTales/security-information-event-management
Author
Rahul Ladumor
Platform Engineer • AWS | DevOps | Cloud Architecture
🌐 Portfolio: https://acloudwithrahul.in
💼 GitHub: https://github.com/rahulladumor
🔗 LinkedIn: https://linkedin.com/in/rahulladumor
📧 Email: rahuldladumor@gmail.com